Firehunter 6000 Sandbox
Advanced Persistent Threats (APTs) often use social engineering to
obtain contact information and send phishing emails to unsuspecting
people. They exploit security vulnerabilities in Internet of Things
(IoT) devices, and hide, without being detected, in high-value
business assets to steal or compromise target information. Attacks
are commonly seen in compromised infrastructure, such as the finance
sector, resource suppliers, and government agencies, affecting
people’s livelihoods. Before launching attacks, perpetrators are
usually well-prepared and wait patiently for their opportunity. Once
attacks are launched, perpetrators usually use technologies, such as
advanced evasion techniques in combination, to exploit known
vulnerabilities. This makes the security devices that detect attack
traffic ineffective.
Huawei FireHunter 6000 series sandbox products (hereinafter referred
to as Huawei FireHunter) are a family of APT detection systems. They
reassemble network traffic mirrored by switches or traditional
security devices, and detect files transferred over networks in
virtualized environments to detect unknown malicious files. Through
credit scanning, real-time behavior analysis, Big Data-based
correlation analysis, and cloud-end technologies, Huawei FireHunter
collects and analyzes the static and dynamic behavior of target
software programs to provide accurate detection results with the
help of Huawei’s unique behavior model library. Based on the
results, Huawei FireHunter detects, blocks, and visualizes
suspicious traffic streams, effectively preventing the spread of
unknown threats and protecting business’s core information assets.
Huawei FireHunter is especially useful to finance and government
agencies, resource providers, and high-tech enterprises.

Characteristic
Multi-system simulation capabilities, ensuring comprehensive
detection of malware and unknown threats
-
Comprehensive traffic detection capabilities: Huawei
FireHunter is capable of identifying mainstream file
transfer protocols, such as HTTP, SMTP, POP3, IMAP, and FTP,
and detecting malicious files transmitted using these
protocols.
-
Detection of mainstream file types: Huawei FireHunter is
capable of detecting malicious codes contained in files,
such as .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pdf, .html,
.js, .exe, .jpg, .gif, .png, and .zip, created using
mainstream applications.
-
Detection of web traffic: Huawei FireHunter supports the
detection of zero-day vulnerabilities on web pages, which
makes Huawei one of just two vendors in the world to support
such a detection function.
-
Simulation of mainstream operating systems and applications:
Huawei FireHunter is capable of simulating the behavior of
Windows operating system, Internet Explorer, Microsoft
Office suite, and Kingsoft WPS by default. This can be
customized to suit your needs.
Multi-layer in-depth detections and rapid response in seconds,
blocking malware and unknown threats
-
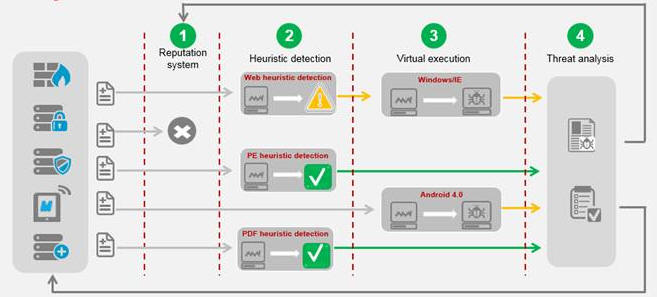
Layered defense system: Huawei FireHunter supports
reputation matching, heuristic detection, and virtualized
execution, ensuring Huawei FireHunter can tackle
next-generation threats represented by APT attacks.
-
Industry-leading performance: Huawei FireHunter provides
industry-leading capability by analyzing 70,000 to 180,000
files per day. Multiple Huawei FireHunters can be deployed
to form a cluster to expand performance.
-
Near-real-time processing capabilities: Huawei FireHunter
provides near-real-time processing capabilities, reducing
the response time from weeks to seconds. In addition, Huawei
FireHunter can work with the NGFW to provide online defense
capabilities.
Multi-dimensional analysis, reducing false positives and
improving the detection accuracy
-
Multi-dimensional analysis capabilities: Huawei FireHunter
pins down suspicious traffic by performing static analysis
that involves the analysis of code snippets and abnormal API
calling, identifies malicious files and operations through
instruction stream monitoring, and determines whether
traffic is legitimate based on intelligent behavior
analysis.
-
High detection accuracy and low false positives: Based on
multi-dimensional analysis, Huawei FireHunter has a
detection accuracy of 99% and reduces false positives using
effective measures, such as a whitelist.
Deployment Scenario
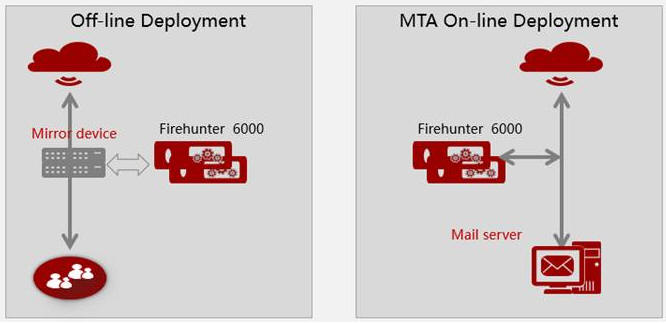
Huawei FireHunter can be deployed in following modes:
Off-line mode: Huawei FireHunter detects malicious files in mirrored
traffic using the mirroring port or optical splitter. If network
traffic is replicated and sent to Huawei FireHunter for analysis,
the firewall or IPS device is responsible for blocking malicious
traffic detected by Huawei FireHunter.
MTA in-line mode: Huawei FireHunter is directly connected to the
email server. After the email server and Huawei FireHunter are
configured to work with each other, Huawei FireHunter detects the
email attachments before forwarding the messages to the email
server. If an attachment is considered malicious, Huawei FireHunter
blocks the email.
Specification
|
Supports 32-bit PE File Inspection
|
Supports 32-bit Windows XP and Windows 7 operating
systems.
|
|
Supports Compressed PE File Inspection
|
Supports the decompression of and threat detection in
ZIP, RAR, GZ, CAB, and 7Z files.
|
|
Supports Compressed Web File Inspection
|
Supports the decompression of and threat detection in
ZIP, RAR, GZ, CAB, and 7Z files.
|
|
Supports PDF File Inspection
|
Supports Adobe Reader 9, X, and XI.
|
|
Supports Compressed PDF File Inspection
|
Supports the decompression of and threat detection in
ZIP, RAR, GZ, CAB, and 7Z files.
|
|
Supports Traffic Restoration of Layer-2 Protocols
|
Supports Layer-2 protocols such as ETH, VLAN, PPTP, PPP,
and PPPOE in traffic restoration.
|
|
Supports Traffic Restoration of Layer-3 and Layer-4
Protocols
|
Layer-3 and Layer-4 protocols supported by traffic
restoration include IPv4, IPv6, GRE, TCP, and UDP.
|
|
Supports Traffic Restoration of Application-layer
Protocols
|
Application-layer protocols supported by traffic
restoration include HTTP, FTP, SMTP, POP3, IMAP, TFTP,
NFS, and Samba.
|
|
Model |
FireHunter 6000 |
|
Hardware Configuration |
• x86 server in a 2U rack
• Memory of no less than 128 GB
• Two power modules for redundancy
• Hard drive with a capacity of no less than 2 TB
• SSD drive with a capacity of no less than 128 GB
|
|
Performance |
• 70,000 files (non-web pages) per day or 36,000 web
pages per hour
• Average detection response time of less than 30
seconds
|


