Carriers, large enterprises, data centers, and large ICPs can now
protect their online services with the world’s first Terabit DDoS
defense. Huawei’s AntiDDoS8000 Series responds within 2 seconds to
more than 100 types of DDoS attacks.
Big Data analytics technologies “teach” systems to learn more than
60 traffic patterns and build a Huawei-proprietary reputation
mechanism to guard against application-layer botnet attacks. Mobile
botnet database defends mobile gateways. Customer-oriented
management and reports improve security.

Designed for carriers, enterprises, data centers, and ICP service providers (including providers for Web portals, online games, online videos, and DNS services), Huawei anti-DDoS solution incorporates extensive experience in network security and full understanding of customer demands.
Huawei anti-DDoS solution enhances defense against application-layer attacks, IPv4-IPv6 attack defense, and defense against zombies, Trojan horses, and worms. This fully ensures network security and service continuity.
Huawei anti-DDoS solution uses the leaser-specific service design for management configuration, which implements a series of functions, including leaser service model learning, leaser configuration, and report self-service. Moreover, IDC operators can provide the anti-DDoS solution for their leasers as an SAAS service to increase the leaser viscosity, improve IDC competitiveness, and add IDC operation profits.
Service-based defense policy
Huawei anti-DDoS solution supports continuously periodic learning and analysis on the service traffic of the Zone, draws the outline of normal service traffic, and enables differentiated defense types and policies for various services or one service in different time ranges, therefore implementing refined defense.
Accurate abnormal traffic cleaning
Huawei anti-DDoS solution uses the per-packet detect technology. Defense is triggered immediately by an attack. This solution applies multiple technologies, including seven-layer filtering, behavior analysis, and session monitoring, to accurately defend against various flood attacks, Web application attacks, DNS attacks, SSL DoS/DDoS attacks, and protocol stack vulnerability attacks. In this way, application servers are protected.
Intelligently caching DNS traffic
Besides accurately defending against various attacks on the DNS server, Huawei anti-DDoS solution supports DNS cache for improved performance under heavy DNS server traffic.
Defense against prevailing zombies/Trojan horses/worms
By spreading Trojan horses and worms to large numbers of hosts, hackers control the hosts hierarchically and form the botnet to launch attacks. Therefore, botnets breed DDoS attacks. Huawei anti-DDoS solution identifies and blocks over 200 common zombies/Trojan horses/worms worldwide, therefore smashing botnets.
Perfect IPv4-IPv6 defense
In February 2011, IANA declared that IPv4 addresses were exhausted. Enterprises have no new IPv4 addresses and begin to put IPv6 network construction into agenda. The particular IPv4-IPv6 technology of Huawei anti-DDoS solution supports concurrent defense against DDoS attacks on both IPv4 and IPv6 networks. The solution addresses the DDoS attack defense requirements in dual stack and helps users transit to the next generation network.
Flexible networking
The anti-DDoS solution must be adaptive to various network
environments and address different grades of service requirements.
On this basis, Huawei anti-DDoS solution provides multiple in-line
and off-line deployments, which enable customers to select
flexibly by their services and networks.
In-line deployment: serially connects the detecting and cleaning
modules to the network to be protected for direct traffic
detecting and cleaning. The high-performance and multi-core hardware
platform in use not only ensures the detecting and
cleaning accuracy, but also minimizes the processing delay.
Moreover, Huawei anti-DDoS solution provides the bypass module.
When an anomaly occurs, traffic is sent to the cleaning module,
which avoids introducing new failures.
Off-line traffic-diversion deployment: deploys the cleaning module
on the network in off-line mode. Once detecting DDoS
attack traffic, the detecting and cleaning centers perform actions
based on the policies configured in the management center.
Highlights of Huawei anti-DDoS solution:
Efficient and speedy: 200 Gbit/s defense performance and response
within seconds
High-performance and multi-core CPU, providing anti-DDoS products
covering 2 Gbit/s to • 200 Gbit/s performance to
defend against all types of DDoS attack.
• Self-learning of the service model and per-packet detect
technology. Once a traffic or packet anomaly is found, the defense
policy is automatically triggered. The defense latency is within two
seconds.
Accurate and comprehensive: "V-ISA" reputation technical system, Can
defend against hundreds of attacks
• "V-ISA" reputation technical system, Can defend against hundreds
of DDoS attacks, with the industry-leading
defense types.
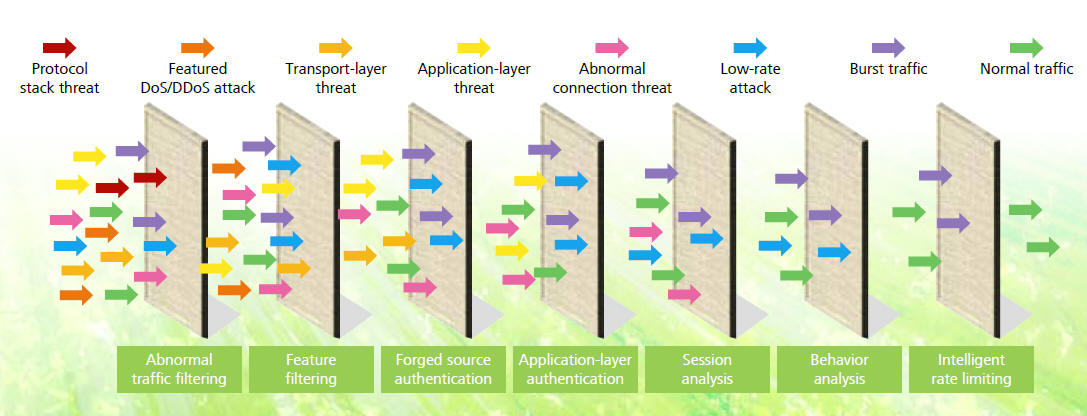
• Defense against over 200 zombies, Trojan horses, and
worms, protecting users from hackers.
• IPv4/IPv6, as the first to support IPv6 attack defense and
concurrent IPv4 and IPv6 attack defense.
• Particular terminal identification technology to accurately
identify client types, such as smart terminals, set-boxes, and
common clients, as well as client-specific defense technologies to
ensure zero false positive.
Value-added operation: protection for tens of thousands of leasers
and diverse self-services
• Leaser-based service design to protect 100,000 leasers
concurrently.
• Self-configuration of defense policies and the generation of
independent security reports, providing visibility into defense
effects.
• Capture of attack packets, extraction of attack features, and
user-defined attack feature filtering to effectively defend
against DDoS attacks and zero-day attacks.
A Metropolitan Area Network (MAN) provides a platform on which comprehensive services of a city are transmitted. MANs often apply to large and medium-sized cities. The MANs provide common and public network architecture and allow data, voice, images, and videos to be effectively transmitted at high speeds, meeting changeable Internet application requirements.
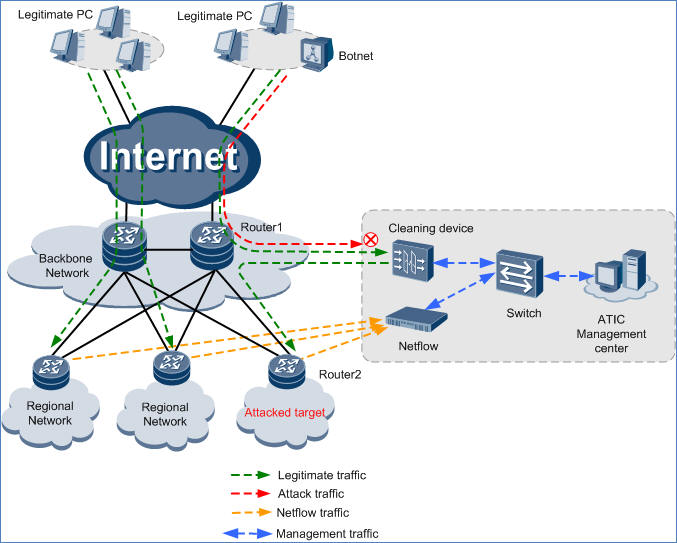
On the network shown in the above figure, a netflow detection device collects the logs from routers in real time to determine whether the traffic in the network is abnormal. When traffic is abnormal, cleaning device is notified to start the cleaning. The cleaning device is attached to the core router, Router 1, to clean traffic destined for the Zone. After cleaning traffic, the cleaning device injects normal traffic back to the original link in MPLS LSP injection mode. Router 2 then forwards the traffic to the Zone.
The cleaning device is directly connected to Router 1 only through one interface. Traffic is diverted to the cleaning device through the main interface, while injected back through a sub-interface. The traffic can also be injected back through another interface if there are enough interfaces.
An Internet Data Center (IDC) is a part of basic network resources. It provides large-scale, high-quality, secure, and reliable data transmission services and high-speed access services for Internet content providers, enterprises, media, and each types of websites. The IDC provides DNS servers, Web servers, game servers, and other services. In recent years, more and more Internet-initiated DDoS attacks target IDCs. As a result, important servers are attacked; data center link bandwidth is occupied; videos and games are compromised by application-layer attacks.
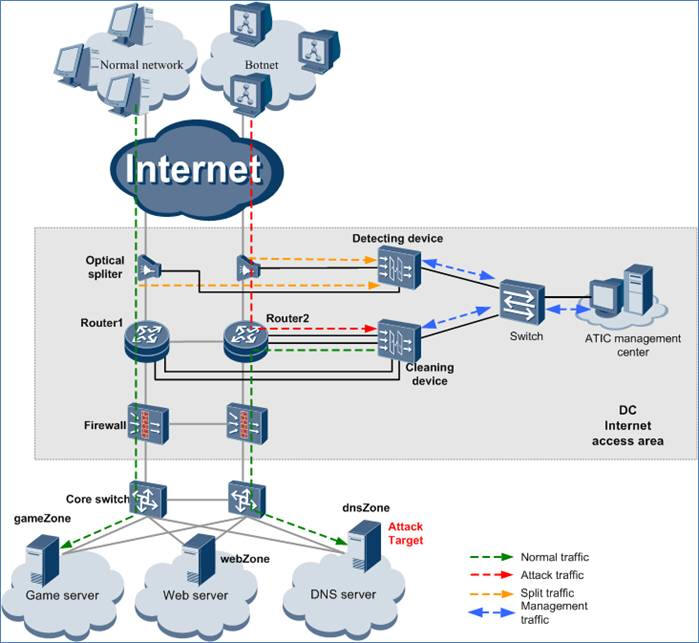
On the network shown in above figure, a cleaning device is attached to the core router 1 and router 2 to detect and clean the traffic destined for the Zone. The traffic must be diverted to the cleaning device using BGP in real time. After traffic is cleaned, normal traffic is injected back to the original link through PBR and finally forwarded to the Zone.
The ATIC management center supports managed security service and can be configured with customized defense policies based on the tenant’s service features. When an attack happens, the ATIC management center can initiate automatic protection and send alarm information by email or other methods. Data center operators can design business models based on tenants and expand business revenue.
| DDoS Defense Specifications | |
|---|---|
|
Defense against
protocol abuse attacks Defense against Land, Fraggle, Smurf, WinNuke, Ping of Death, Teardrop, and TCP error flag attacks |
Web application
protection Defense against HTTP GET flood, HTTP POST flood, HTTP slow header, HTTP slow post, HTTPS flood, SSL DoS/DDoS, WordPress reflection amplification, RUDY, and LOIC attacks; packet validity check |
|
Defense against
scanning and sniffing attacks Defense against address and port scanning attacks, and attacks using Tracert packets and IP options, such as IP source route, timestamp, and record route |
DNS application
protection Defense against DNS query flood, DNS reply flood, and DNS cache poisoning attacks; source limit |
|
Defense against
network-type attacks Defense against SYN flood, SYN-ACK flood ACK flood, FIN flood, RST flood, TCP fragment flood, UDP flood, UDP fragment flood, IP flood, ICMP flood, TCP connection flood, sockstress, TCP retransmission, and TCP empty connection attacks |
SIP application
protection Defense against SIP flood/SIP methods flood attacks, including Register, Deregistration, Authentication, and Call flood attacks; source limit |
|
Defense against
UDP-based reflection amplification attacks Defense against NTP, DNS, SSDP, Chargen, TFTP, SNMP, NetBIOS, QOTD, Quake Network Protocol, Portmapper, Microsoft SQL Resolution Service, RIPv1, and Steam Protocol reflection amplification attacks |
Filter IP, TCP, UDP, ICMP, DNS, SIP, and HTTP packet filters |
|
Location-based
filtering Traffic block or limit based on the source IP address location |
|
|
Attack signature
database RUDY, slowhttptest, slowloris, LOIC, AnonCannon, RefRef, ApacheKill, and ApacheBench attack signature databases; automatic weekly update of these signature databases |
IP reputation Tracking of most active 5 million zombies and automatic daily update of the IP reputation database to rapidly block attacks; local access IP reputation learning to create dynamic IP reputation based on local service sessions, rapidly forward service access traffic, and enhance user experience |
| Management and Reporting | |
|---|---|
|
Management
functions Account management and permission allocation; defense policy configuration and report display based on Zones (up to 100,000 Zones, namely tenants); device performance monitoring; source tracing and fingerprint extraction through packet capture; email, short message, and audio alarms; log dumping; dynamic baseline learning |
Report functions Comparison of traffic before and after cleaning; top N traffic statistics; application-layer traffic comparison and distribution; protocol distribution; traffic statistics based on the source location; attack event details; top N attack events (by duration or number of packets); distribution of attacks by category; attack traffic trend; DNS resolution success ratio; application-layer top N traffic statistics (by source IP address, HTTP URI, HTTP HOST, and domain name); download of reports in HTML/PDF/Excel format; report push via email; periodical generation of daily, weekly, monthly, and yearly reports |
| Traffic Diversion and Injection | |
|---|---|
|
Traffic
diversion Supports manual, and PBR or BGP based automatic traffic diversion |
Traffic
injection Supports static route injection, MPLS VPN injection, MPLS LSP injection, GRE tunnel injection, Layer 2 injection, PBR based injection, etc |
Hardware Specifications
| Model | AntiDDoS8030 | AntiDDoS8080 | AntiDDoS8160 |
|---|---|---|---|
| Interfaces and performance | |||
| Throughput | Up to 120 Gbit/s | Up to 720 Gbit/s | Up to 1,440 Gbit/s |
| Throughput/Slot | Up to 80 Gbit/s | Up to 160 Gbit/s | Up to 160 Gbit/s |
| Mitigation Rate/Slot | Up to 60 Mpps | Up to 60 Mpps | Up to 60 Mpps |
| Latency | 80 μs | 80 μs | 80 μs |
| Expansion Slots | 3 | 8 | 16 |
| Expansion LPU | FW-LPUF-120, 2 sub-slots |
FW-LPUF-120, 2 sub-slots FW-LPUF-240, 2 sub-slots |
FW-LPUF-120, 2 sub-slots FW-LPUF-240, 2 sub-slots |
| Expansion Interfaces | 24 x GE (SFP); 5 x 10 GE (SFP+); 6 x 10 GE (SFP+); 12 x 10 GE (SFP+); 1 x 40 GE (CFP); 1 x 100 GE (CFP) | ||
| Dimensions | |||
| Height x Width x Depth |
DC: 175 mm x 442 mm x 650 mm (4U) AC: 220 mm x 442 mm x 650 mm (5U) |
620 mm x 442 mm x 650 mm (14U) | 1,420 mm x 442 mm x 650 mm (32U) |
| Weight |
DC chassis: 15 kg (empty), 30.7 kg (full) AC chassis: 25 kg (empty), 40.7 kg (full) |
43.2 kg (empty), 112.9 kg (full) | 94.4 kg (empty), 233.9 kg (full) |
| Power and Environment | |||
| Power Supply |
Rated input voltage: DC: -48V AC: 175V to 264V; 50 Hz/60 Hz Maximum input voltage range: DC: -72V to -38V AC: 90V to 264V; 50 Hz/60 Hz |
Rated input voltage: DC: -48V AC: 175V to 264V; 50 Hz/60 Hz Maximum input voltage range: DC: -72V to -38V AC: 90V to 264V; 50 Hz/60 Hz |
Rated input voltage: DC: -48V AC: 175V to 264V; 50 Hz/60 Hz Maximum input voltage range: DC: -72V to -38V AC: 90V to 264V; 50 Hz/60 Hz |
| Power Consumption |
1 x FW-LPUF-120 + 2 x ADS-SPUC-B + 2 x ADS-SPC-80-01: DC: 1,066W (avg.), 1,272W (max.) AC: 1,185W (avg.), 1,414W (max.) |
3 x FW-LPUF-240 + 5 x ADS-SPUD-B + 10 x ADS-SPC-80-01: DC: 4,025W (avg.), 4,823W (max.) AC: 4,282W (avg.), 5,132W (max.) |
6 x FW-LPUF-240 + 9 x ADS-SPUD-B + 18 x ADS-SPC-80-01: DC: 7,387W (avg.), 8,930W (max.) AC: 7,858W (avg.), 9,500W (max.) |
| Power Redundancy |
DC: Double hot-swappable power modules AC: Double hot-swappable power modules |
DC: 4 hot-swappable PEM modules AC: 4 PEM modules + 1 external AC power chassis |
DC: 8 hot-swappable PEM modules AC: 8 PEM modules + 2 external AC power chassis |
| Operating Temperature | 0°C to 45°C (long-term), -5°C to 50°C (short-term) | ||
| Storage Temperature | -40°C to 70°C | ||
| Operating Humidity | 5% RH to 85% RH, non-condensing (long-term), 5% RH to 95% RH, non-condensing (short-term) | ||
| Storage Humidity | 0% RH to 95% RH | ||
| Certifications | |||
| Safety Certifications |
Electro Magnetic Compatibility (EMC) certification CB, Rohs, FCC, MET, C-tick, and VCCI certification |
||
| AntiDDoS8000 Series | ||
|---|---|---|
| AntiDDoS8030 | ||
| AntiDDoS8030-BASE-DC | AntiDDoS8030 DC Basic Configuration (includes X3 DC Chassis, 2 x MPU), with HW General Security Platform Software | Alternative |
| AntiDDoS8030-BASE-AC | AntiDDoS8030 DC Basic Configuration (includes X3 DC Chassis, 2 x MPU), with HW General Security Platform Software | |
| AntiDDoS8080 | ||
| AntiDDoS8080-BASE-DC | AntiDDoS8080 DC Basic Configuration (includes X8 DC Chassis, 2 x SRU, 1 x SFU), with HW General Security Platform Software | Mandatory |
| CR52-PWRA-AC-DF | AC Distribution Frame for Cabinet, 2 or 6 Inputs, 6(2 x 3) Outputs, 6 Groups of 2 Poles 20A Air Switch | AC mandatory |
| USG9500-PWR-AC | AC Power Supply Module | AC mandatory |
| AntiDDoS8160 | ||
| AntiDDoS8160-BASE-DC | AntiDDoS8160 DC Basic Configuration (includes X16 DC Chassis, 2 x MPU, 4 x SFU), with HW General Security Platform Software | Mandatory |
| CR52-PWRA-AC-DF | AC Distribution Frame for Cabinet, 2 or 6 Inputs, 6(2 x 3) Outputs, 6 Group of 2 Poles 20A Air Switch | AC mandatory |
| USG9500-PWR-AC | AC Power Supply Module | AC mandatory |
| SPU of the AntiDDoS 8000 series | ||
| ADS-SPUA01 | Service Processing Unit, Double CPUs, with HW General Security Platform Software | Optional (the SPU must be used with a license) |
| LIC-ADS-10GDDD00 | Capability for Detector (a multiple of 10G), with HW General Security Platform Software | |
| LIC-ADS-10GDDC00 | Capability for Cleaning (a multiple of 10G), with HW General Security Platform Software | |
| ADS-SPUA02 | Service Processing Unit, Four CPUs, with HW General Security Platform Software | Optional (the SPU must be used with a license) |
| LIC-ADS-20GDDD00 | Capability for Detector (a multiple of 20G), with HW General Security Platform Software | |
| LIC-ADS-20GDDC00 | Capability for Cleaning (a multiple of 20G), with HW General Security Platform Software | |
| LPU of the AntiDDoS 8000 series | ||
| LPUF40 | ||
| FWCD0LPUF40A01 | Flexible Card Line Processing Unit (LPUF-40, 2 sub-slots) A, with HW General Security Platform Software | Optional |
| FWCD00L2XX01 | 2-Port 10G Base LAN/WAN-XFP Flexible Card (P40) | Optional |
| FWCD00EFGF01 | 20-Port 100/1,000 Base-X-SFP Flexible Card (P40) | Optional |
| LPUF21 | ||
| FWCD0LPUKD01 | Flexible Card Line Processing Unit (LPUF-21, 2 Sub-Slots) B, with HW General Security Platform Software | Optional |
| FWCD00L1XX01 | 1-Port 10G Base WAN/LAN XFP Flexible Interface Daughter Card, with HW General Security Platform Software | Optional |
| FWCD00EBGF01 | 12-Port 100/1,000 Base-X SFP Flexible Interface Daughter Card, with HW General Security Platform Software | Optional |
| FWCD00EBGE01 | 12-Port 10/100/1,000 Base-TX RJ45 Flexible Interface Daughter Card, with HW General Security Platform Software | Optional |
| FWCD0P1XBZ01 | 1 Port OC-192c/STM-64c POS-XFP Flexible Card, with HW General Security Platform Software | Optional |
| Anti-DDoS components | ||
| ADSERVER-OS-EN | Windows English Platform (AC PC Server, Hard Disk,Microsoft Windows Server, English), including OS License | Optional |
| G0MYSQL02 | System Application Software, Light Application Data Management Software Package (5.5 S), 1 Year Standard Product Services | Optional |
| NS19MKM00 | USB KB&Mouse, Monitor 19-Inch TFT LCD, Max. Pels 1,280 x 1,024/75 Hz, 100V to 240V AC Power, No Documentation, Black | Optional |
| Anti-DDoS management center | ||
| LIC-ADS-NOFA00 | ATIC Basic Feature Summary, with HW General Security Platform Software | Alternative |
| LIC-ADS-DOFA00 | ATIC Operation Feature Summary, with HW General Security Platform Software (including professional DNS defense) | |
| Subrack optical splitter | ||
| OOS314S00 | Optical Splitter, Single Mode, Supports Three Optical Links (1 x 4 each), 1,310/1,550 nm, +/-40 nm, 70:10:10:10, LC/UPC, 0.25 mm, SMF-28e, 180.3 mm x 144.45 mm x 18.1 mm | Optional |
| OOS412S00 | Optical Splitter, Single Mode, Supports Four Optical Links (1 x 2 each), 1,310/1,550 nm, +/-40 nm, 80:20, LC/UPC, 0.25 mm, SMF-28e, 0.2 dB, 180.3 mm x 144.45 mm x 18.1 mm | Optional |
| OOS413S00 | Optical Splitter, Single Mode, Supports Four Optical Links (1 x 3 each), 1,310/1,550 nm, +/-40 nm, 70:15:15, LC/UPC, 0.25 mm, SMF-28e, 180.3 mm x 144.45 mm x 18.1 mm | Optional |
| OOS412M00 | Optical Splitter, Multi-mode, Supports Four Optical Links (1 x 2 each), 850 nm, +/-40 nm, 50:50, LC/UPC, 0.25 mm, 62.5/125ume, 250um loose tube, 0.2 dB, 180.3 mm x 144.45 mm x 18.1 mm | Optional |
| OOSSMRC00 | Optical Splitter, Single Mode/Multi-mode, Rack-mounted Optical Splitter Chassis (Used with Optical Splitter Cards), 850/1,310/1550 nm, 482.6 mm x 209 mm x 43.6 mm | Optional |
| OOS412S01 | Optical Splitter, Single Mode, Supports Four Optical Links (1 x 2 each), 1,310/1,550 nm, +/-40 nm, 50:50, LC/UPC, 0.25 mm, SMF-28e, 0.2 dB, 180.3 mm x 144.45 mm x 18.1mm | Optional |